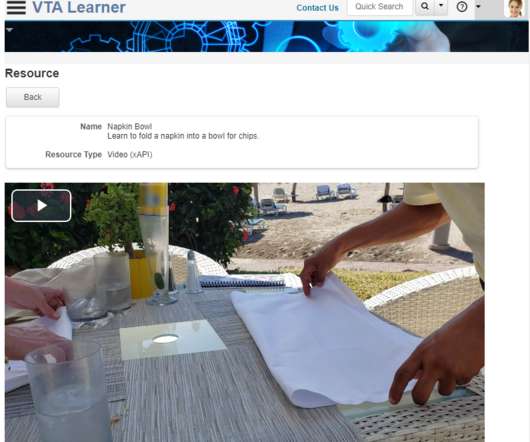
xAPI Video Profile in Resource Videos
RISC
JANUARY 6, 2020
RISC has long supported YouTube videos in the VTA Resource feature. We realize that many customers cannot link to YouTube videos due to corporate policy. For this reason, we have now created support for Resource videos that reside elsewhere, even behind your firewall. This support includes xAPI statements to track usage.


















































Let's personalize your content