Cyber Security Requirements

From protecting your assets from malicious attacks to safeguarding your team from digital fraud like phishing and identity theft, cyber security has many battlefronts, which is why it must remain robust. Below, you’ll find a list of cyber security requirements that you and your team should prioritize to steer clear of unhelpful stress and potential losses from cyber attacks.
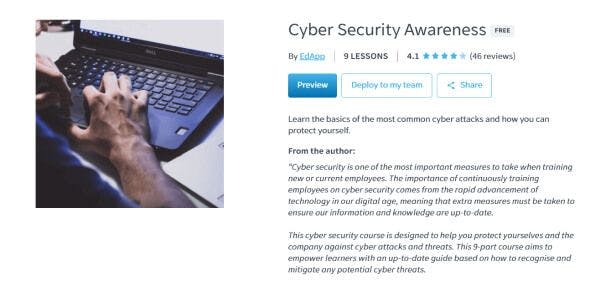
1. Increase cyber security awareness
The importance of education and awareness of cyber security can’t be stressed enough. Apart from having robust security systems in place, having a team that’s well equipped with cyber security skills and knowledge will be your best defense against cyber-criminal activities. Data breaches from human error and negligence can cost millions, while holding a cyber security awareness program is far more practical and relatively more affordable. Some corporate training platforms even offer free cyber security courses that won’t cost you a penny.

But what are the requirements of cyber security? If you’re unsure of where to start, EdApp can lend a hand in training and educating your team about cyber security and its role in protecting company and personal assets. Signing up to this platform will give you access to their free courses like Cyber Security and Cyber Security Awareness, which are both ready to be delivered to your team. These resources can help introduce your team to the basics of cyber security, its role and importance in the workplace, as well as some tips and best practices to protect systems from data breaches. These courses also come fully editable. To tweak its content and rebrand it as needed, feel free to make use of EdApp’s creator tool.
Sign up for Free and Start Using The Best Cyber Security Training Platform!
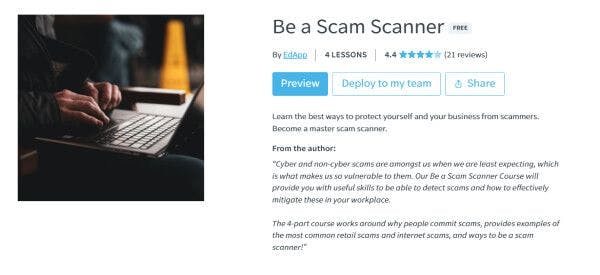
2. Learn more about different cyber attacks
Another one of the cyber security requirements to consider is making sure that your team knows and understands the threat landscape or the entirety of potential cyber threats they’re most likely to face. Educate them on how attackers can gain access to their data through different mediums like emails, web browsing, file transfers, as well as calls and texts. It’s also a good idea to go over the different signs of potential danger with your team, as well as the appropriate steps to take in response.

EdApp’s Be a Scam Scanner courses can guide your teams through the most common internet scams and strategies to avoid them. You can also check its course on Cybersecurity & Internal Threats if you want to educate your team about threats or attacks that may come from inside your organization. This course delves into the many types of internal threats, outlines some helpful tricks to spot an insider threat, and touches on insider threat management. To help with retention, both of these courses follow a microlearning design model. They are also quick and easy to follow, and learners will only need at least 4-5 minutes to complete each lesson.
3. Keep your software and devices up to date
Cyber threats are constantly evolving and becoming more complex as the days pass by. For this reason, software developers have been working to keep their products up to date to make sure that their users will be able to stay on top of the most common and most recent cybercrimes.
Software updates often contain new security features and security patches, which must be installed to fix potential security holes and safeguard your assets from unknown data access.
Similarly, the operating systems of your devices should also be updated regularly to support these software upgrades. Updating devices will also remove any outdated features and make them less prone to hackers and unauthorized access.
Most of the new devices and apps today can automatically install updates, making this cyber security requirement pretty much fuss-free for everyone on your team. Still, it would be good practice to keep an eye out in case there are any device or software updates that require the user’s assistance.
4. Amp up cyber prevention practices
Prevention is better than cure, and this saying is even more true when it comes to cyber security. There are a variety of ways that can help amp up your cyber prevention practices. One option is to employ IT experts who will be on top of all the security measures needed to detect and prevent attackers from accessing your database. If you don’t have enough time and resources to do so, then you might want to consider looking into cyber monitoring tools, like Intrusion Detection Systems (IDS). These programs are built to detect suspicious activities, and once they do, they’ll send an alert or email notification to an administrator. It’s also worth exploring Advanced Threat Protection (ATP) services, which can help spot advanced and next-gen attack types that traditional security software isn’t capable of detecting.

5. Invest in anti-virus software and firewall
Another way to amp up your cyber security prevention practices is by investing in anti-viruses and firewalls. Anyone involved in cyber security will agree that these two mechanisms are the pillars of a strong cyber security posture. Antiviruses protect systems by detecting viruses or malicious links and files, while firewalls act as barriers that prevent attackers and criminals from reaching your database in the very first place. Without them, you’re basically leaving your systems open to cyber-attacks and account breaches.

The need for these products is even more vital than ever before, given how quickly the world of cybercrime is expanding today. Luckily, the market now has a wide array of firewalls and anti-virus software products that can help prevent hackers from reaching your organization’s database.
If you’re unfamiliar with these security products, we recommend checking Kaspersky’s What to Look for In an Antivirus Software: Choosing Protection for an Android, Mac or Windows System, which will guide you and your team through the most important elements and factors when choosing antivirus software. Experts from SecurEdge have also compiled a guide about 7 Key Points to Consider When Purchasing a New Firewall that will help you find the best firewall out there.
6. Improve password hygiene
Passwords play a very important role in keeping systems and databases safe and secure from hackers and malicious attackers. In fact, having strong passwords is the best way to keep cyber criminals at bay, as it greatly reduces the likelihood of them gaining access to your company’s account.

There are some tips that you and your team should know to achieve this requirement for cyber security. First and foremost, it’s important to use different, unique passwords for each device and account. As a rule of thumb, passwords should be kept long and complex, preferably with a combination of uppercase and lowercase letters, numbers, and symbols. Personal information like birthdays and a family member’s name should also be avoided, as they’re by far the easiest to crack.
There are several tools that can also help generate strong passwords, and most of them provide their services for free. Password vaults are also a thing now. Like a vault, these programs are designed to store passwords in a secure digital location. Users, in turn, are only required to master a single password, and the vault will provide the passwords for all the accounts or applications that must be accessed.
7. Backup your data
Data backup is also one of the crucial cybersecurity requirements. This process involves the idea of copying and storing sensitive data in a separate location, like a tape drive, USB, or cloud storage. The primary purpose of this practice is to have a secure archive that can be easily restored in case of data loss. Examples of data loss scenarios include hardware failures, such as a hard drive making a clicking noise, malware or virus attacks, and accidental deletion. When you have backup data, it will be easier to recover from such an unfortunate event and minimize the expense of such unplanned downtime.

Creating a backup copy isn’t a one-time thing – it must be part of your regular cyber security hygiene and information security programs. Organizations gather new data almost every day. The longer you wait between data backups, the more data you risk losing. Make it a habit among your team to store, archive, and create backups, including backup for Hyper-V environments, on a consistent and regular basis.. Having multiple copies stored in different storage systems and retaining physical copies are also good backup strategies.
8. Avoid public wifi security risks
Wifi hotspots in public spaces like coffee shops, libraries, hotels, and airports are often, if not always, unsecured. Since their connection is open to everyone, there’s not a lot that can be done to block attackers from hacking and getting into your account. These criminals can either steal both personal and business data or, worse, infect your device with malware and conduct pretty much any crime that they want.

Advising your team to stay away from public wifi would be the most practical way to fulfill this cyber security requirement. But in special cases when they need to work outside of their workstations, there are also some precautions that can improve their security and fend hackers off. They can use a virtual private network (VPN) connection to hide their IP address and encrypt their data. A firewall and antivirus software can also help protect their laptops from malware and suspicious activities. Good practices like accessing only secured websites, turning off the sharing option from system preferences, and not accessing sensitive information when connected to public networks can also go a long way in preventing cyber crimes from occurring.
9. Improve mobile security
Working professionals have benefited greatly from the advancement of mobile devices. Thanks to these pocket-sized devices, work is basically just within the reach of their fingertips. But this convenience comes at a price – mobile devices have now become a valuable target for hackers. This is where the importance of mobile security comes into the picture.

Fortunately, mobile security combined with responsible practices isn’t exactly as tricky as protecting software and hardware. Simple countermeasures such as locking phones with a unique passcode, encrypting sensitive data, and installing antivirus software will be able to protect these hand-held devices from hacking attempts. Best yet, the majority of smartphones today are now built with good mobile security software that updates regularly and automatically to patch security holes and keep hackers out.
10. Re-evaluate your cyber security practices
Routine maintenance of monitoring of your cyber security posture is also a vital cyber security requirement. Cyber attacks are getting smarter and more sophisticated as time passes, so your old cyber security measures may no longer be as effective as they once were. With this in mind, it would be a good habit to regularly re-evaluate your cyber hygiene. Examine which tools and procedures are still effective and which are not, identify security holes, and learn about the most current cyber attacks and how to counter them.

Running a refresher on cyber security training will also help your team remember the concepts that they may have already forgotten. You can also use this opportunity to go over new tools and security features and practices that you’re planning to reinforce.
Refresher training platform EdApp has an array of solutions that can help boost your refresher training and tools to improve the learner experience. They have a powerful course creator tool that can help transform your content into short but highly engaging slides. All you need to do is drag and drop your content, apply your branding and you’re all set! You can also create quizzes in a game-style format, and enable gamification elements like leaderboards, timers, and rewards to make your training, even more, fun and exciting.
Author
Jeanellie Avelino
Jen is a learning expert at EdApp, a mobile-based training platform that helps corporates and businesses bring their training solutions to the next level. She carries an extensive writing experience in a variety of fields, including architecture, the gig economy, and computer software. Outside of work, she enjoys her free time watching her favorite series and documentaries, reading motivational books, and cross-stitching.
