Is training really the answer? Ask the flowchart.
Making Change
MAY 7, 2023
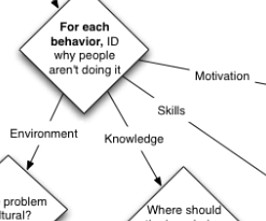
By Cathy Moore Here's a flowchart that will help you identify the best solution to a performance problem, whether it's a job aid, a workflow improvement, training, or something else. It's based on action mapping , my streamlined approach to instructional design. Get the flowchart: PDF or interactive First, download the flowchart.














































Let's personalize your content