Maximizing Success: The Strategic Advantage of Global Talent Outsourcing
Infopro Learning
MAY 29, 2024
This flexibility enables companies to secure the ideal talent for their unique requirements, irrespective of geographical limitations. To protect against this risk, businesses can implement legal contracts and agreements that clearly define ownership rights and confidentiality obligations.









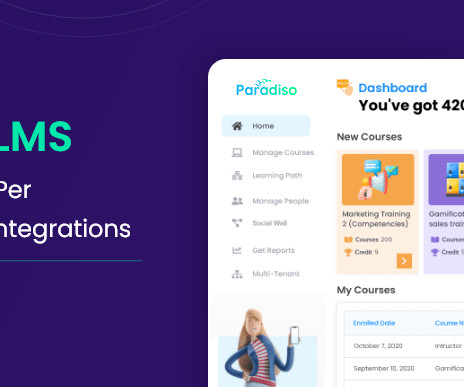




















Let's personalize your content